Exploring AWS AI: Transforming the Future of Technology
Exploring AWS AI: Transforming the Future of Technology
Amazon Web Services (AWS) has been at the forefront of cloud computing for years, and its suite of artificial intelligence (AI) services is no exception. AWS AI offers a range of powerful tools designed to help businesses and developers build intelligent applications with ease.
What is AWS AI?
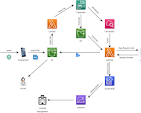
AWS AI encompasses a variety of machine learning and artificial intelligence services that allow users to integrate advanced capabilities into their applications. From natural language processing to image recognition, AWS provides scalable solutions that cater to diverse needs.
Key Services Offered by AWS AI
- Amazon SageMaker: A comprehensive service that enables data scientists and developers to build, train, and deploy machine learning models quickly. SageMaker simplifies the entire machine learning process by providing built-in algorithms and easy-to-use interfaces.
- Amazon Rekognition: This service offers image and video analysis capabilities, allowing users to identify objects, people, text, scenes, and activities within visual content. It’s widely used in security applications and media analysis.
- Amazon Lex: A service for building conversational interfaces using voice and text. Lex powers Amazon Alexa and can be used to create chatbots for customer service or personal assistants.
- Amazon Polly: A text-to-speech service that turns written content into lifelike speech. Polly supports multiple languages and can be customized for various use cases.
- Amazon Comprehend: This natural language processing service helps extract insights from text data by identifying key phrases, sentiments, entities, and language syntax.
The Benefits of Using AWS AI
AWS AI provides numerous advantages for businesses looking to leverage artificial intelligence:
- Scalability: With AWS’s robust infrastructure, businesses can scale their AI solutions effortlessly as their needs grow.
- Cost-Effectiveness: Pay-as-you-go pricing models ensure that companies only pay for what they use, making it accessible even for small businesses.
- Simplified Development: Pre-trained models and APIs reduce the complexity involved in developing AI-powered applications.
- Diverse Use Cases: From healthcare to finance, retail to entertainment, AWS AI services cater to a wide array of industries.
The Future of AWS AI
AWS continues to invest heavily in research and development to enhance its AI offerings. With advancements in deep learning frameworks and increased integration with other AWS services like IoT (Internet of Things), the future holds exciting possibilities for innovation across various sectors.
The adoption of artificial intelligence is set to revolutionize how businesses operate globally. By leveraging AWS’s state-of-the-art technology stack combined with its vast ecosystem support network – companies are better positioned than ever before when embarking on their digital transformation journeys powered by intelligent automation solutions provided through this platform!
If you’re interested in exploring what these cutting-edge technologies have offer your organization today – consider diving deeper into world-leading cloud-based solutions offered exclusively via Amazon Web Services’ Artificial Intelligence suite!
9 Advantages of AWS AI: Scalable, Cost-Effective, and Secure Solutions for Modern Businesses
- Scalable AI solutions to meet varying business needs.
- Cost-effective pay-as-you-go pricing model.
- Easy integration with existing AWS services and infrastructure.
- Streamlined development process with pre-trained models and APIs.
- Wide range of AI services catering to different use cases.
- Robust security measures for protecting sensitive data.
- Continuous innovation and updates to enhance AI capabilities.
- Support for multiple programming languages and frameworks.
- Global reach with data centers in multiple regions for low-latency access.
Top 5 Challenges of Using AWS AI: Learning Curve, Cost, Connectivity, Privacy, and Customization
- 1. Learning Curve
- 2. Cost
- 3. Dependency on Internet Connectivity
- 4. Data Privacy Concerns
- 5. Customization Limitations
Scalable AI solutions to meet varying business needs.
AWS AI provides scalable solutions that are designed to meet the varying needs of businesses, regardless of their size or industry. With AWS’s robust cloud infrastructure, companies can easily scale their AI applications up or down based on demand. This flexibility ensures that businesses can efficiently handle peak workloads without overcommitting resources during quieter periods. By leveraging AWS’s pay-as-you-go pricing model, organizations can optimize costs while maintaining the ability to quickly adapt to changing market conditions and customer requirements. This scalability not only supports growth but also empowers businesses to innovate and experiment with new AI-driven strategies without the risk of significant upfront investments.
Cost-effective pay-as-you-go pricing model.
One of the standout advantages of AWS AI is its cost-effective pay-as-you-go pricing model, which makes advanced artificial intelligence accessible to businesses of all sizes. This flexible approach allows companies to only pay for the resources they actually use, eliminating the need for significant upfront investments in hardware or software. By minimizing wasted expenditure and maximizing efficiency, businesses can experiment with and deploy AI solutions without financial risk. This model not only supports startups and small businesses in their innovation efforts but also enables larger enterprises to scale their AI capabilities according to demand, ensuring that costs align closely with usage and business growth.
Easy integration with existing AWS services and infrastructure.
AWS AI offers seamless integration with existing AWS services and infrastructure, making it a highly attractive option for businesses already utilizing the AWS ecosystem. This compatibility allows organizations to effortlessly incorporate AI capabilities into their current workflows without the need for extensive reconfiguration or additional resources. By leveraging AWS’s robust suite of services, such as Amazon S3 for storage, Amazon EC2 for compute power, and Amazon RDS for database management, businesses can enhance their operations with AI-driven insights and automation. This cohesive environment not only accelerates the deployment of AI applications but also ensures a more efficient and streamlined process, ultimately leading to faster innovation and improved business outcomes.
Streamlined development process with pre-trained models and APIs.
AWS AI significantly streamlines the development process by providing pre-trained models and APIs, which allow developers to integrate advanced AI capabilities into their applications without needing extensive expertise in machine learning. These pre-trained models cover a wide range of tasks, from image recognition to natural language processing, enabling developers to quickly deploy intelligent features with minimal effort. By leveraging these ready-to-use tools, businesses can accelerate their development timelines, reduce costs associated with building custom models from scratch, and focus more on refining their applications’ unique functionalities. This approach not only enhances productivity but also empowers companies to innovate faster and deliver AI-powered solutions that meet evolving market demands.
Wide range of AI services catering to different use cases.
AWS AI provides a wide range of services that cater to diverse use cases, making it an ideal choice for businesses across various industries. Whether it’s natural language processing, computer vision, or predictive analytics, AWS offers specialized tools like Amazon Comprehend, Amazon Rekognition, and Amazon Forecast to meet specific needs. This versatility allows companies to integrate AI capabilities seamlessly into their operations, enhancing productivity and innovation. By providing solutions that address unique challenges in fields such as healthcare, finance, retail, and more, AWS enables organizations to harness the power of artificial intelligence effectively and efficiently.
Robust security measures for protecting sensitive data.
AWS AI offers robust security measures designed to protect sensitive data, ensuring that businesses can confidently deploy AI solutions without compromising on data integrity or privacy. With AWS’s comprehensive security framework, users benefit from advanced encryption techniques for data both at rest and in transit. Additionally, AWS provides fine-grained access controls, allowing organizations to define and manage user permissions effectively. Regular compliance audits and certifications further reinforce AWS’s commitment to maintaining high security standards. These measures collectively ensure that sensitive information is safeguarded against unauthorized access and potential breaches, making AWS AI a trusted choice for organizations handling critical data.
Continuous innovation and updates to enhance AI capabilities.
AWS AI is renowned for its commitment to continuous innovation and frequent updates, which significantly enhance its AI capabilities. By consistently integrating the latest advancements in machine learning and artificial intelligence, AWS ensures that its users have access to cutting-edge tools and technologies. This ongoing evolution allows businesses to stay ahead of the curve, leveraging new features that improve efficiency, accuracy, and scalability. With AWS’s robust infrastructure and dedication to research and development, organizations can confidently build intelligent applications that meet the ever-changing demands of the market, ensuring they remain competitive in a rapidly evolving technological landscape.
Support for multiple programming languages and frameworks.
AWS AI offers extensive support for multiple programming languages and frameworks, making it a versatile choice for developers across various skill levels and backgrounds. This flexibility allows developers to work in their preferred language, whether it’s Python, Java, C++, or others, ensuring seamless integration with existing projects. Additionally, AWS AI is compatible with popular machine learning frameworks such as TensorFlow, PyTorch, and Apache MXNet. This broad compatibility not only accelerates the development process but also empowers teams to leverage existing expertise and resources. By accommodating a wide range of programming environments, AWS AI enables businesses to innovate rapidly and efficiently deploy AI solutions that meet their specific needs.
Global reach with data centers in multiple regions for low-latency access.
One of the significant advantages of AWS AI is its global reach, facilitated by a vast network of data centers strategically located in multiple regions worldwide. This extensive infrastructure ensures that users can access AI services with minimal latency, regardless of their geographical location. By distributing data centers across different regions, AWS provides faster response times and improved performance for applications, enabling businesses to deliver seamless user experiences to their customers. This low-latency access is particularly beneficial for applications that require real-time processing and quick data retrieval, making AWS AI an ideal choice for companies operating on a global scale.
1. Learning Curve
One of the notable challenges associated with AWS AI services is the steep learning curve they present, particularly for beginners. While AWS offers a comprehensive suite of powerful tools and services, understanding how to effectively utilize these resources can be daunting for those new to cloud computing or artificial intelligence. The complexity arises from the need to grasp various concepts, configurations, and integrations that AWS AI entails. Users often need to invest significant time and effort into learning the platform’s intricacies, which can include mastering its interface, understanding its pricing models, and navigating through its extensive documentation. This initial hurdle may slow down adoption for individuals or organizations without prior experience in similar technologies, potentially delaying project timelines as they work to build the necessary expertise.
2. Cost
While AWS AI offers a robust suite of tools and services, one significant consideration is the potential cost involved, particularly for large-scale projects or high usage volumes. Implementing AI solutions on AWS can become expensive as businesses scale their operations or require extensive computational resources. The pay-as-you-go pricing model, while flexible, may lead to unforeseen expenses if not carefully managed. This can be especially challenging for startups or smaller companies with limited budgets, who might find it difficult to predict costs accurately as their needs evolve. Therefore, it’s crucial for organizations to thoroughly assess their usage patterns and optimize their resource allocation to mitigate potential financial impacts when utilizing AWS AI services.
3. Dependency on Internet Connectivity
One of the significant drawbacks of AWS AI services is their dependency on internet connectivity. Since these services are cloud-based, a stable and reliable internet connection is essential for seamless operation. Without consistent connectivity, users may experience disruptions in accessing AI tools and applications, leading to potential delays in processing data or executing tasks. This reliance can be particularly challenging for businesses operating in regions with unreliable internet infrastructure or during network outages. Consequently, organizations must ensure robust internet solutions are in place to fully leverage the capabilities of AWS AI services without interruption.
4. Data Privacy Concerns
When utilizing AWS AI services, one significant concern is data privacy. Storing sensitive data on cloud servers inherently raises potential security and privacy risks that must be meticulously managed. While AWS implements robust security measures to protect data, the responsibility of ensuring compliance with privacy regulations and safeguarding against unauthorized access falls partly on the user. This includes configuring access controls, encrypting data, and regularly monitoring for vulnerabilities. Organizations must carefully assess their data protection strategies and ensure they adhere to relevant legal standards to mitigate any potential risks associated with cloud storage. Balancing the benefits of AWS AI with these privacy considerations is crucial for maintaining trust and security in digital operations.
5. Customization Limitations
One potential drawback of using AWS AI is its customization limitations. While AWS provides a range of pre-built models and APIs that simplify the integration of artificial intelligence into applications, these tools may not offer the flexibility needed for highly specialized use cases. As a result, businesses seeking to implement tailored functionalities could find themselves constrained by the default settings and capabilities provided by AWS. This can be particularly challenging for organizations with unique requirements that demand significant customization beyond what standard models allow. Consequently, while AWS AI is highly efficient for general purposes, those needing more bespoke solutions might need to explore additional options or invest in further development to meet their specific needs.