Agile Software Development: Principles and Practices Based on Flexibility and Collaboration
Agile Software Development: Principles and Practices
Agile software development is a methodology that emphasizes flexibility, collaboration, and continuous improvement in the software development process. It is based on a set of principles and practices that enable teams to respond to change quickly and deliver high-quality software efficiently.
Key Principles of Agile Software Development
Agile software development is based on the following key principles:
- Customer Collaboration: Agile teams prioritize customer satisfaction by involving customers in the development process and adapting to their changing needs.
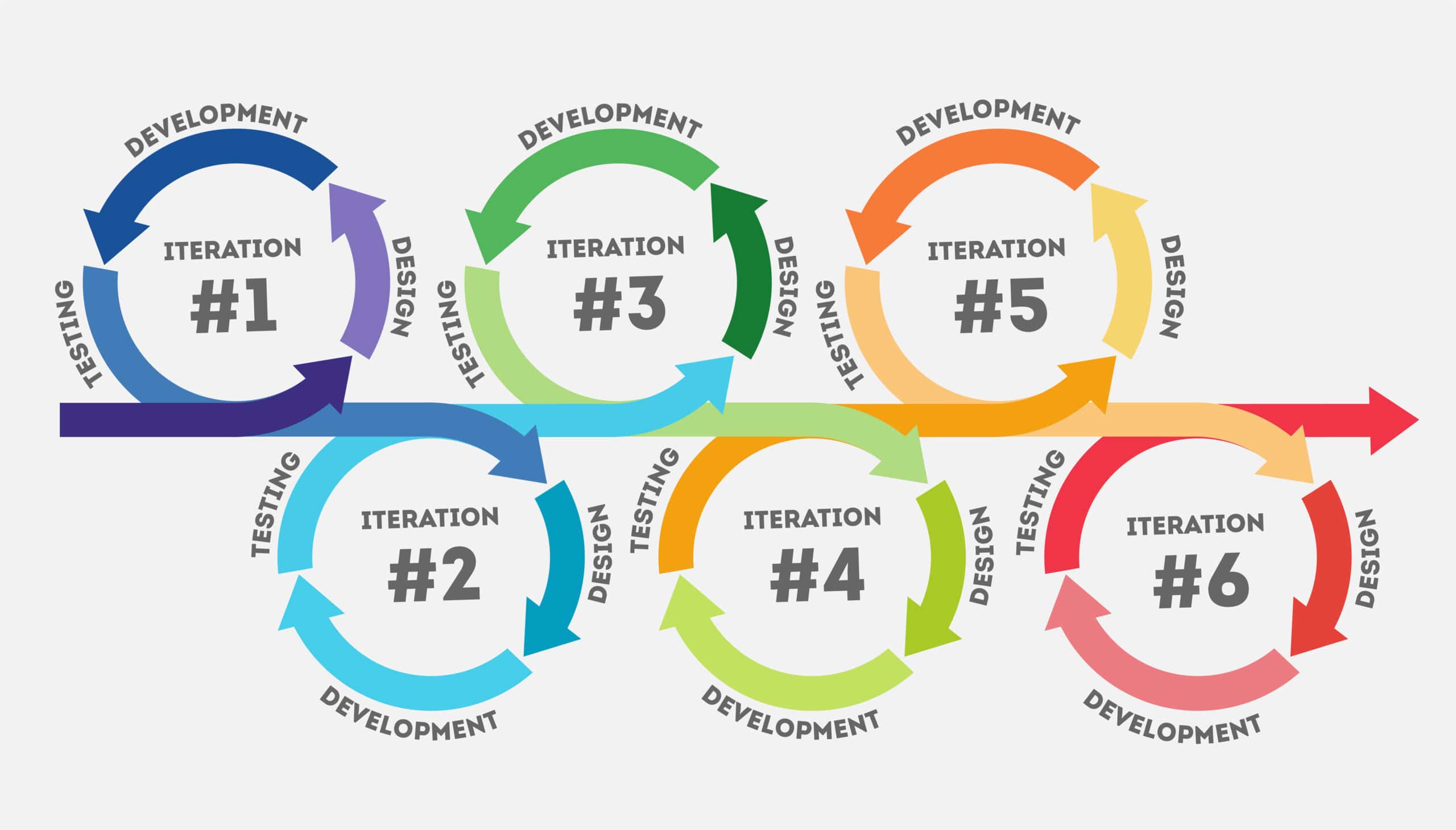
- Iterative Development: Agile projects are broken down into small, manageable increments called iterations or sprints. This allows for quick feedback and adjustments throughout the development cycle.
- Adaptability: Agile teams embrace change and are flexible in responding to new requirements or priorities as they arise.
- Cross-Functional Teams: Agile teams are composed of individuals with diverse skills who work together collaboratively to achieve project goals.
Practices of Agile Software Development
In addition to its core principles, agile software development relies on a set of practices to guide teams in implementing these principles effectively. Some common agile practices include:
- Daily Stand-up Meetings: Team members meet briefly each day to discuss progress, challenges, and plans for the day.
- User Stories: Requirements are captured as user stories, which describe features from the user’s perspective.
- Sprint Planning: Teams plan their work for each sprint, setting goals and prioritizing tasks based on customer value.
- Continuous Integration: Code changes are integrated frequently to detect issues early and ensure smooth collaboration among team members.
In conclusion, agile software development is a dynamic approach that empowers teams to deliver value quickly and adapt to changing requirements with ease. By embracing its principles and practices, organizations can build high-quality software that meets customer needs efficiently and effectively.
Understanding Agile Software Development: Process Models, Core Principles, and Key Elements
- Is Agile based software development a software process model?
- Is Agile software development based on iterative or incremental?
- What are the 4 core principles of Agile methodology?
- What are the 3 key elements of Agile methodology?
- What are the 5 principles of agile?
- What is the agile model based on?
Is Agile based software development a software process model?
Agile software development is not a traditional software process model in the strict sense. Instead, it is a flexible and iterative approach to software development that focuses on delivering value to customers through collaboration, adaptability, and continuous improvement. While traditional software process models, such as Waterfall or V-Model, follow a structured sequence of phases, Agile emphasizes responding to change and customer feedback throughout the development cycle. Agile is more about embracing principles and practices that promote agility and efficiency rather than adhering to a rigid process model.
Is Agile software development based on iterative or incremental?
Agile software development is based on both iterative and incremental approaches. Iterative development involves breaking down the project into smaller iterations or cycles, where each iteration delivers a working piece of the software. This allows for quick feedback, adjustments, and improvements throughout the development process. On the other hand, incremental development focuses on continuously adding new features and functionalities to the software in a step-by-step manner. By combining both iterative and incremental practices, Agile teams can deliver value to customers more efficiently and adapt to changing requirements effectively.
What are the 4 core principles of Agile methodology?
The four core principles of Agile methodology serve as the foundation for its approach to software development. These principles include customer collaboration, iterative development, adaptability, and cross-functional teams. Customer collaboration emphasizes the importance of involving customers in the development process to ensure their satisfaction. Iterative development breaks down projects into manageable increments for quick feedback and adjustments. Adaptability allows teams to embrace change and respond to new requirements effectively. Lastly, cross-functional teams bring together individuals with diverse skills to work collaboratively towards project goals, promoting efficiency and innovation in the Agile development process.
What are the 3 key elements of Agile methodology?
In Agile methodology, the three key elements that form its foundation are transparency, inspection, and adaptation. Transparency ensures that all aspects of the project are visible and understandable to everyone involved, promoting open communication and collaboration. Inspection involves regularly assessing progress and quality to identify any issues or deviations from the project’s goals, allowing for timely adjustments. Adaptation emphasizes the flexibility to respond to changing requirements or priorities throughout the development process, enabling teams to deliver value efficiently and effectively. By embracing these key elements, Agile methodology enables teams to work iteratively, deliver high-quality software, and continuously improve their processes.
What are the 5 principles of agile?
In agile software development, the five key principles that form the foundation of the methodology are customer collaboration, iterative development, adaptability, cross-functional teams, and responding to change. These principles emphasize the importance of engaging customers throughout the development process, breaking down projects into manageable iterations for quick feedback and adjustments, embracing change as a natural part of the process, fostering collaboration among team members with diverse skills, and being flexible in adapting to evolving requirements. By adhering to these principles, agile teams can effectively deliver high-quality software that meets customer needs in a dynamic and responsive manner.
What is the agile model based on?
The agile model is based on a set of core principles and values that prioritize customer collaboration, iterative development, adaptability, and cross-functional teamwork. This methodology emphasizes flexibility, responsiveness to change, and continuous improvement throughout the software development process. By breaking down projects into smaller increments, fostering close collaboration with customers, and embracing evolving requirements, the agile model enables teams to deliver high-quality software efficiently and effectively.