Exploring the Synergy Between Machine Learning and Deep Learning
The Power of Machine Learning and Deep Learning
Machine learning and deep learning are two transformative technologies that have revolutionized various industries, from healthcare to finance to transportation. These cutting-edge fields of artificial intelligence have the potential to unlock new possibilities and drive innovation like never before.
Machine Learning
Machine learning is a subset of artificial intelligence that enables systems to learn from data and improve their performance without being explicitly programmed. By analyzing patterns in data, machine learning algorithms can make predictions or decisions with minimal human intervention. This technology is widely used in applications such as recommendation systems, fraud detection, and image recognition.
Key Concepts in Machine Learning:
- Supervised Learning: Algorithms learn from labeled training data to make predictions or classifications.
- Unsupervised Learning: Algorithms find patterns in unlabeled data without predefined outcomes.
- Reinforcement Learning: Agents learn by interacting with an environment and receiving rewards or penalties based on their actions.
Deep Learning
Deep learning is a subset of machine learning that uses artificial neural networks with multiple layers to model complex relationships in data. These deep neural networks can automatically discover intricate patterns and features, leading to state-of-the-art performance in tasks like natural language processing, computer vision, and speech recognition.
Advantages of Deep Learning:
- Hierarchical Feature Representation: Deep neural networks can learn hierarchical representations of data, capturing intricate features at different levels of abstraction.
- Scalability: Deep learning models can scale with more data and computational resources, allowing for continuous improvement in performance.
- Versatility: Deep learning architectures can be adapted to various domains and tasks, making them highly versatile for diverse applications.
In conclusion, machine learning and deep learning are driving the next wave of technological advancements across industries. As these fields continue to evolve, we can expect even more groundbreaking innovations that will shape the future of AI-driven solutions.
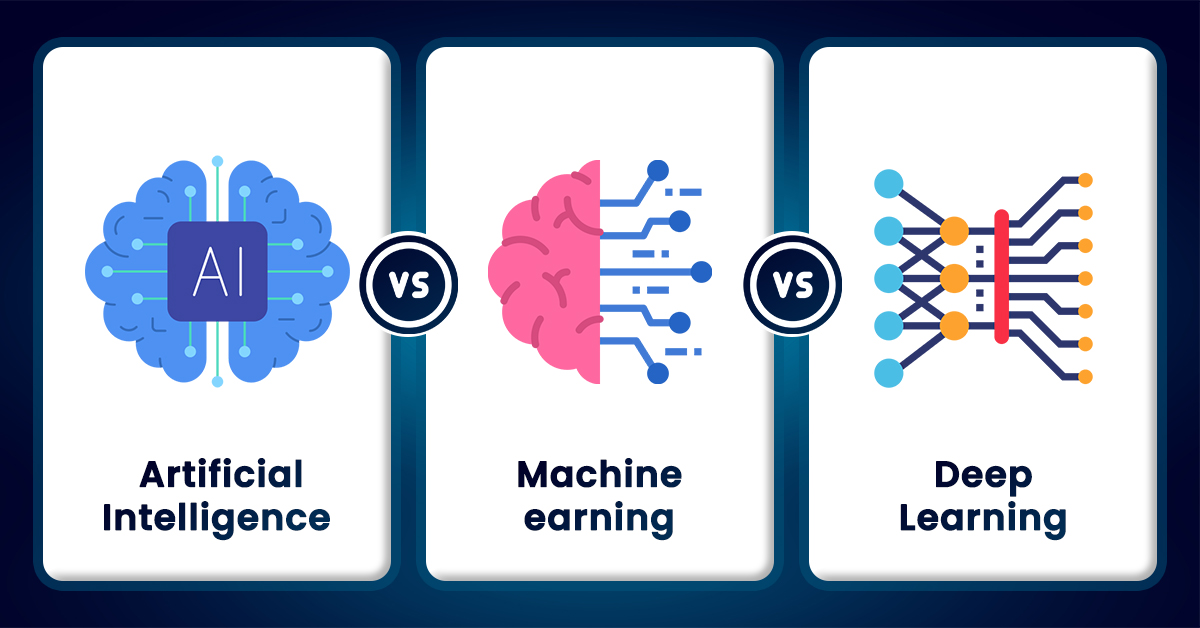
Understanding the Differences: ML vs DL vs NLP vs AI
- What is ML vs DL vs NLP?
- What is the difference between machine learning and deep learning?
- Does deep learning require machine learning?
- What is ML vs DL vs AI?
- What is the difference between deep learning and machine learning?
- What is the difference between AI ML and DL?
What is ML vs DL vs NLP?
When discussing machine learning (ML), deep learning (DL), and natural language processing (NLP), it’s essential to understand their distinctions. Machine learning is a broader concept that encompasses various algorithms and techniques enabling systems to learn from data and make predictions. Deep learning is a subset of machine learning that uses neural networks with multiple layers to model complex patterns in data, achieving high levels of accuracy in tasks like image recognition and speech synthesis. Natural language processing focuses specifically on the interaction between computers and human language, allowing machines to understand, interpret, and generate human language. In essence, ML provides the foundation for DL, which in turn powers advanced applications like NLP, showcasing the interconnected nature of these technologies in shaping the future of artificial intelligence.
What is the difference between machine learning and deep learning?
When exploring the distinction between machine learning and deep learning, it is essential to understand that machine learning is a broader concept that encompasses various techniques for enabling computers to learn from data and make decisions without explicit programming. On the other hand, deep learning is a subset of machine learning that specifically focuses on artificial neural networks with multiple layers to model complex patterns and relationships in data. While machine learning algorithms can handle a wide range of tasks based on labeled or unlabeled data, deep learning excels in processing vast amounts of unstructured data for tasks like image recognition, natural language processing, and speech recognition. In summary, deep learning is a sophisticated approach within the realm of machine learning that leverages deep neural networks to achieve high levels of accuracy and performance in complex tasks requiring intricate pattern recognition.
Does deep learning require machine learning?
In the realm of artificial intelligence, deep learning is actually a subset of machine learning. Therefore, deep learning does require machine learning as a foundational concept. Machine learning encompasses various algorithms and techniques that enable systems to learn from data and make predictions or decisions without explicit programming. Deep learning, on the other hand, utilizes complex neural networks with multiple layers to model intricate patterns in data. So, while deep learning is a specialized form of machine learning, it builds upon the core principles and methodologies of machine learning to achieve advanced levels of performance in tasks such as image recognition, natural language processing, and more.
What is ML vs DL vs AI?
Machine Learning (ML), Deep Learning (DL), and Artificial Intelligence (AI) are interconnected fields that often cause confusion due to their overlapping nature. AI is the broadest concept, encompassing any technique that enables machines to mimic human intelligence. Within AI, machine learning is a subset focused on creating algorithms that allow computers to learn from and make predictions based on data. Deep learning, in turn, is a specialized subset of machine learning that uses neural networks with multiple layers to analyze complex patterns in large datasets. While AI can include rule-based systems and other non-learning techniques, ML and DL specifically refer to data-driven approaches where systems improve over time with exposure to more data.
What is the difference between deep learning and machine learning?
When discussing the difference between deep learning and machine learning, it’s important to understand that deep learning is a subset of machine learning. While both technologies involve training algorithms to make predictions based on data, the key distinction lies in their approach to data representation and feature extraction. Machine learning algorithms typically require manual feature engineering to extract relevant patterns from data, whereas deep learning models use artificial neural networks with multiple layers to automatically learn hierarchical representations of data. This allows deep learning algorithms to capture intricate features at different levels of abstraction, leading to superior performance in complex tasks such as image recognition and natural language processing. In essence, deep learning can be seen as a more advanced and sophisticated form of machine learning that leverages deep neural networks for unparalleled predictive power.
What is the difference between AI ML and DL?
Artificial Intelligence (AI), Machine Learning (ML), and Deep Learning (DL) are interconnected fields, but they differ in scope and complexity. AI is the broadest concept, encompassing any technique that enables machines to mimic human intelligence. Within AI, machine learning is a subset that focuses on algorithms allowing computers to learn from data and improve their performance over time without being explicitly programmed. Deep learning, in turn, is a specialized subset of machine learning that uses neural networks with multiple layers to analyze complex patterns in large datasets. While AI provides the overarching goal of creating intelligent systems, ML offers the methods for data-driven learning, and DL enhances these methods by enabling more sophisticated pattern recognition through deep neural networks.