Unlocking Business Potential with Custom-Made Software Solutions
The Power of Custom-Made Software Solutions
In today’s fast-paced digital world, off-the-shelf software solutions may not always meet the unique needs of businesses. This is where custom-made software comes into play, offering tailored solutions that address specific requirements and challenges.
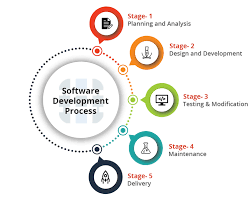
Custom-made software is designed and developed to fit the exact specifications of a business or organization. Unlike pre-packaged software, custom solutions are built from the ground up, considering the specific workflows, processes, and goals of the client.
Benefits of Custom-Made Software:
- Enhanced Efficiency: Custom software streamlines processes and eliminates unnecessary steps, leading to increased productivity and efficiency.
- Scalability: Custom solutions can easily adapt to the evolving needs of a business, allowing for seamless scalability as the organization grows.
- Improved Integration: Custom software can be seamlessly integrated with existing systems and applications, ensuring smooth data flow and communication across different platforms.
- Greater Security: Tailored security features can be implemented to protect sensitive data and prevent cyber threats, enhancing overall data security.
- Cost-Effectiveness: While custom software development may involve an initial investment, it often proves to be cost-effective in the long run by eliminating the need for multiple off-the-shelf solutions and reducing inefficiencies.
Whether it’s a customer relationship management (CRM) system, inventory management software, or a bespoke mobile application, custom-made software offers businesses a competitive edge by providing tailored solutions that align with their unique requirements.
In conclusion, custom-made software plays a crucial role in helping businesses optimize their operations, improve efficiency, and achieve their strategic objectives. By investing in custom solutions that are designed specifically for their needs, organizations can unlock new opportunities for growth and success in today’s digital landscape.
9 Essential Tips for Successful Custom Software Development
- Clearly define your requirements before starting the custom software development process.
- Choose an experienced and reputable software development company or team.
- Regularly communicate with the developers to ensure alignment with your vision.
- Prioritize security measures to protect your data and users.
- Plan for scalability to accommodate future growth and changes in your business.
- Allocate sufficient time and budget for thorough testing and quality assurance.
- Provide training for end-users to ensure successful adoption of the custom software.
- Establish a maintenance plan to address any issues or updates post-launch.
- Continuously gather feedback from users to make improvements and updates as needed.
Clearly define your requirements before starting the custom software development process.
It is essential to clearly define your requirements before embarking on the custom software development process. By outlining your specific needs, objectives, and expectations upfront, you provide a solid foundation for the development team to create a solution that precisely aligns with your business goals. Clear requirements help streamline the development process, reduce misunderstandings, and ensure that the final product meets your exact specifications. Investing time in defining your requirements at the outset can lead to a more efficient and successful custom software development journey.
Choose an experienced and reputable software development company or team.
When opting for custom-made software solutions, it is crucial to select an experienced and reputable software development company or team. Working with professionals who have a proven track record in custom software development ensures that your project is in capable hands. An experienced team will not only possess the technical expertise needed to bring your vision to life but also offer valuable insights and guidance throughout the development process. By choosing a reputable software development partner, you can have confidence in the quality of the final product and ensure that your custom software meets your unique requirements effectively.
Regularly communicate with the developers to ensure alignment with your vision.
Regular communication with the developers throughout the custom software development process is crucial to ensure that the end product aligns with your vision and requirements. By maintaining an open line of communication, you can provide feedback, clarify expectations, and address any concerns promptly. This collaborative approach helps to foster a strong partnership between you and the developers, ultimately leading to a custom software solution that meets your specific needs and delivers optimal results.
Prioritize security measures to protect your data and users.
When developing custom-made software, it is crucial to prioritize security measures to safeguard your data and users. Implementing robust security features helps prevent unauthorized access, data breaches, and other cyber threats that could compromise sensitive information. By prioritizing security in the development process, you can ensure the integrity and confidentiality of your data, build trust with users, and mitigate potential risks associated with cyber attacks.
Plan for scalability to accommodate future growth and changes in your business.
When developing custom-made software, it is essential to plan for scalability to accommodate future growth and changes in your business. By designing the software with scalability in mind, you can ensure that the system can easily expand and adapt to meet the evolving needs of your organization. This proactive approach not only saves time and resources in the long run but also enables your software to support your business’s growth trajectory effectively.
Allocate sufficient time and budget for thorough testing and quality assurance.
When developing custom-made software, it is essential to allocate sufficient time and budget for thorough testing and quality assurance. Testing plays a crucial role in identifying and resolving any issues or bugs in the software before it is deployed. By investing in comprehensive testing processes, businesses can ensure that their custom software meets high standards of functionality, performance, and security. This proactive approach not only helps prevent potential problems but also contributes to the overall success and reliability of the software solution.
Provide training for end-users to ensure successful adoption of the custom software.
To ensure the successful adoption of custom-made software, it is essential to provide training for end-users. By offering comprehensive training sessions, users can familiarize themselves with the new software’s features and functionalities, ultimately increasing their proficiency and confidence in utilizing the system effectively. Training not only enhances user experience but also promotes a smoother transition to the custom software, maximizing its benefits and ensuring that it aligns with the organization’s goals and requirements.
Establish a maintenance plan to address any issues or updates post-launch.
Establishing a maintenance plan is crucial when it comes to custom-made software. This plan ensures that any issues or updates that arise post-launch are promptly addressed, maintaining the software’s functionality and performance over time. By proactively managing maintenance tasks, businesses can prevent potential disruptions, enhance user experience, and ensure that the software continues to meet their evolving needs effectively. A well-defined maintenance plan is essential for maximizing the longevity and value of custom software solutions.
Continuously gather feedback from users to make improvements and updates as needed.
To ensure the success and relevance of custom-made software, it is essential to continuously gather feedback from users. By actively seeking input and insights from those who interact with the software on a regular basis, developers can identify areas for improvement and make necessary updates to enhance user experience. This iterative process of feedback collection and implementation helps in refining the software, addressing user needs effectively, and ensuring that the solution evolves to meet changing requirements over time.